Explaining the hidden "Google Hangouts" Chrome extension
Table of Contents
According to Luca Casonato on Twitter, every Chromium-based browser leaks information about your computer to domains owned by Google.
Let's dig a little deeper into this.
How it works
There is a hidden extension deep in the Chromium source code named "Google Hangouts". You cannot see or uninstall this extension, but you can read it's source code on the Chromium documentation.
Looking into the manifest_v3.json file, we can see that this extension only works on domains ending with .google.com:
// ...
"externally_connectable": {
"matches": [
"https://*.google.com/*"
]
}Digging deeper, it appears that this extension listens for 2 events:
chrome.runtime.onConnectExternal.addListener(function(port) {
if (port.name === 'chooseDesktopMedia') {
onChooseDesktopMediaPort(port);
} else if (port.name === 'processCpu') {
onProcessCpu(port); // Process the received data.
} else {
// Unknown port type.
port.disconnect();
}
});The processCpu event forwards the received data to websites who ask for it.
What data is being monitored
The received data includes:
- CPU name, usage and features
- Individual tabs CPU/GPU usage, memory allocated and memory used
While this could be used for fingerprinting, the only place we could find this functionality being used is the Google Meet app.
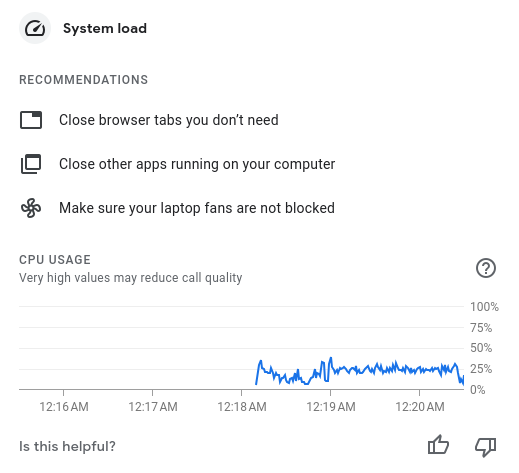
Since this information is only available in the context of Chrome extensions, this just seems like a little hack for better Google Meet troubleshooting. Still, it's strange that all Google domains are allowed to access this information.
Other browsers like Microsoft Edge and Brave also have this same extension, since they are based on Chromium.
Inspecting some of the data
You can see some of the data that's being sent by going to any website under the google.com domain and pasting the following code into your Chrome devtools console:
chrome.runtime.sendMessage(
'nkeimhogjdpnpccoofpliimaahmaaome', {
method: 'cpu.getInfo'
}, response => {
console.log('CPU Info:\n', JSON.stringify(response, null, 2));
}
);This code snippet calls the cpu.getInfo method in the extension and returns the result. nkeimhogjdpnpccoofpliimaahmaaome is the extension id. This will only work on Google domains.
For example, here are the results I got:
{
"value": {
"archName": "x86_64",
"features": [
"mmx",
"sse",
"sse2",
"sse3",
"ssse3",
"sse4_1",
"sse4_2",
"avx"
],
"modelName": "Intel(R) Core(TM) i5-8300H CPU @ 2.30GHz",
"numOfProcessors": 8,
"processors": [
{
"usage": {
"idle": 635385,
"kernel": 12822,
"total": 688437,
"user": 40230
}
},
// ...
],
"temperatures": []
}
}Keep in mind that any Chrome extension with the proper permissions can read your CPU usage. The System CPU Usage extension on the Chrome web store does just that.
This isn't a security risk or anything, but the fact that all Google sites can read system information that other sites can't just feels wrong.
Resources
You can read more about this on the HackerNews discussion or you can just read the source code behind this extension.